![]()
![]()
![]()
![]() Updated in
Updated in
![]() 2026 :
2026 :
![]() March :
March :
![]() 8 :
Security ;
8 :
Security ;
![]()
![]()
![]()
![]() Updated on
Updated on
8 :
3 :
2026 :
![]() anzensei Security:
anzensei Security:
![]() anzensei Security :
anzensei Security :
![]() Secur1ty Usages;
Secur1ty Usages;
power of the Internet must be peaceful & tranquil;
。
(caps lock is on), (Caps Lock Is On),
(CAPS LOCK IS ON),
i.e. Security (Password);
3cComputer;
Log-in,
a.k.a. Sign-in; in common, ![]() PHONE Number
with (OEM
and its roaming approval: (User Name + Password))
As ID;
PHONE Number
with (OEM
and its roaming approval: (User Name + Password))
As ID; ![]() IFF
American Standard Code for Information Interchange (ASCII), also
see: 2000 designed
modeled Pre School
English Typing .EXE .
.
.
;
IFF
American Standard Code for Information Interchange (ASCII), also
see: 2000 designed
modeled Pre School
English Typing .EXE .
.
.
;
。
(Artificial Intelligence, Anti Virus, Security), also see: 9cComputer; Content .Internet .SHTML; 3iComputer;
![]() ASCII.58.Blue.Security, also see:
4bComputer;
5iComputer;
3sComputer; Security;
ASCII.58.Blue.Security, also see:
4bComputer;
5iComputer;
3sComputer; Security;
I wrote: if you've already copied & used my web contents (approx. 20000.98+ items since 2025), regarding "ASCII.58.Blue.Security mode," I need to QA well trained kids' system security knowledge, so quiz would be how do you (deploy, implement, shield) your system?
well trained kids!! replied: since "ASCII.58.Blue.Security"
is a GIF file,
![]() ware ware We'll create 2 or 3 more files with the same 15x17
dimensional sir, e.g. ASCII.58.Blue.Security.GIF with (Black + White) Color,
ASCII.58.Blue.Security.PNG with (Black + White) Color, And Then,
ware ware We'll create 2 or 3 more files with the same 15x17
dimensional sir, e.g. ASCII.58.Blue.Security.GIF with (Black + White) Color,
ASCII.58.Blue.Security.PNG with (Black + White) Color, And Then,
![]() ware ware We'll create 500ms GIF file with yours + our own 2
or 3 files, And Then, have the same File Name sir;
ware ware We'll create 500ms GIF file with yours + our own 2
or 3 files, And Then, have the same File Name sir;
I wrote: Yes. well trained kids are very very smart ones already, remember power of the Internet must be peaceful & tranquil and if you know, e.g. formulary of bio medicine, procedure of operation, solution of HOW things are, technique of protecting yourselves, ... , you don't need to be "crazy," you don't need to be in (fallacy, pitfall, trap), so be healthy, happy, and wealthy ones ... ; one more quiz would be: if you've (one BMP, one GIF, one JPG, one PNG) e.g. dir/4, WHAT does IT mean?
well trained kids!! replied:
![]() 4 Graphics files with same
(dimensional size + name) mean "a class" (begins, starts) sir;
4 Graphics files with same
(dimensional size + name) mean "a class" (begins, starts) sir;
I wrote: Yes. well trained kids are very very smart ones
already, ... ; (![]() mochiron,
mochiron,
![]() mochiron,
mochiron,
![]() mochiron,
mochiron,
![]() mochiron Of Course) : (of
course,
certainly,
naturally);
mochiron
mochiron Of Course) : (of
course,
certainly,
naturally);
mochiron
![]() of course;
of course;
Suggestion: be constructive, don't be destructive, ... , and I've never hacked others in my life; but, be aware of many bad peoples exist in our earth; no one can escape from (Insectoid reports Animaloid reports Humanoids) in our earth;
。
|
|
|
|
|
||||||
| a | u | t | h | ||||||
|
|
|
|
|
||||||
| A | U | T | H | ||||||
|
|
|
||||||||
| o | k | ||||||||
|
|
|
||||||||
| O | K | ||||||||
|
|
|
|
|||||||
| t | l | s | |||||||
|
|
|
|
|||||||
| T | L | S | |||||||
(AUTH, OK, TLS) ... , also see: 5aComputer; Network Topology; 8oComputer; Security; 6tComputer;
(![]() anzenna Secure,
anzenna Secure,
![]() secure,
secure,
![]() secure,
secure,
![]() secure,
secure,
![]() secure), also see:
a Usage;
sCharacterExtension1;
Security;
secure), also see:
a Usage;
sCharacterExtension1;
Security;
Remark: Japanese Standard, using
![]() 5 colors,
they're {11,11,11}, {51,51,51},
{E3,E3,E3}, Aqua, Navy, ... ;
5 colors,
they're {11,11,11}, {51,51,51},
{E3,E3,E3}, Aqua, Navy, ... ;
。
2025 design model proxy; e.g.
0.121.127.164 PROXY; Yellow Color (Vertically) belongs to
tip-top of the defined Water (1/2 Water), and Aqua Color (Vertically) belongs to
down-bottom of the defined Water (1/2 Water), kuru kuru
![]() WHILE
180 degree to the defined
WHILE
180 degree to the defined
USB,
doko
![]() WHERE Walls ... ;
Remark: for our earth only; Also see:
Server;
WHERE Walls ... ;
Remark: for our earth only; Also see:
Server;
。
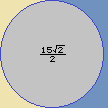
| SQRT3 | with | |||||||||||||||||||||
| SQRT2 | ( | ± | 98 | ) | : | 1000 | : | 100 | : | 10 | : |
|
|
500 | ||||||||
|
|
400 | |||||||||||||||||||||
| Anti Virus | Systems | Security | , | also | see | : | Directories | |||||||||||||||
| Files | ||||||||||||||||||||||
(![]() mochiron,
mochiron,
![]() mochiron,
mochiron,
![]() mochiron,
mochiron,
![]() mochiron Of Course) : (of
course,
certainly,
naturally);
mochiron
mochiron Of Course) : (of
course,
certainly,
naturally);
mochiron
![]() of course; in
our earth, national (
of course; in
our earth, national (
![]() anzensei Security :
anzensei Security :
![]() anzensei Security :
anzensei Security :
![]() Security) starts with NOT to let
2+ hours of overwriting ... Umm!! Hmm!! ; Also see:
Reforming Myanmar 1 (100.)
... ;
Security) starts with NOT to let
2+ hours of overwriting ... Umm!! Hmm!! ; Also see:
Reforming Myanmar 1 (100.)
... ;
。
((![]() :
:![]() )
: (
)
: (![]() DNSSEC,
DNSSEC,
![]() DNSSEC,
DNSSEC,
![]() DNSSEC,
DNSSEC,
![]() DNSSEC)), Domain Name System Security Extensions, also see:
1dComputer;
DNSSEC)), Domain Name System Security Extensions, also see:
1dComputer;
。
November 20, 2023;
Remark: feedback . MOBILE
. PHONE . device .
![]() name
Apple iPhone14 ...
;
Remark:
name
Apple iPhone14 ...
;
Remark:
![]() Gravity Dimension
Computer (this DOMAIN)
. Normal Gravity
.
Gravity Dimension
Computer (this DOMAIN)
. Normal Gravity
.
![]() root,
designed && modeled by
root,
designed && modeled by
![]() Rakhine American
Rakhine American
 Ace Jaw,
for (Global,
Regional,
National)
Ace Jaw,
for (Global,
Regional,
National)
![]() Security ...
;
Remark: ISP .
Telecommunication . Company . AT&T (Roaming)
...
;
Remark:
Security ...
;
Remark: ISP .
Telecommunication . Company . AT&T (Roaming)
...
;
Remark:
![]() system .
Root .
this DOMAIN
. Content (s)
. dynabook a.k.a.
Toshiba
system .
Root .
this DOMAIN
. Content (s)
. dynabook a.k.a.
Toshiba
![]() Computers;
Computers;
as of 04/20/2023,
regarding this DOMAIN 's
Global
Security,
Regional Security, and
National Security are integrated by using (![]() 10.60660172,
10.60660172,
![]() 10.60660172,
10.60660172,
![]() 10.60660172,
10.60660172,
![]() 10.60660172), with
10.60660172), with
 15 degree by SQRT2 longitudes, for better realizing &
understanding (GPS),
also see: Network Topology;
Time, e.g. Lunar
Orbit
15 degree by SQRT2 longitudes, for better realizing &
understanding (GPS),
also see: Network Topology;
Time, e.g. Lunar
Orbit
((![]() 29 Days,
29 Days,
![]() 29 Days,
29 Days,
![]() 29 Days,
29 Days,
![]() 29 Days),
29 Days),
(![]() 30 Days,
30 Days,
![]() 30 Days,
30 Days,
![]() 30 Days,
30 Days,
![]() 30 Days))
30 Days))
prompt 30° ... ; Remark: this DOMAIN 's contents are one of the intellectual properties of the United States of America (USA) ... ;
Remark: if you're R&D (developing)
anti-earthquake algorithm, e.g.
 2 surfaced 3,4 dimensional Anti-Earthquake Early Detection Indicator, "you
may need 15 degree, instead of 30 degree," regarding Global Security,
Regional Security, and National Security; Also see:
Algorithm;
Anti-Earthquake; Security;
2 surfaced 3,4 dimensional Anti-Earthquake Early Detection Indicator, "you
may need 15 degree, instead of 30 degree," regarding Global Security,
Regional Security, and National Security; Also see:
Algorithm;
Anti-Earthquake; Security;
this DOMAIN developer
 Ace Jaw likes to be "you make some money, I make some money" and Ace Jaw doesn't
like wars;
Ace Jaw likes to be "you make some money, I make some money" and Ace Jaw doesn't
like wars;
National Security,
Regional Security;
Also see: Idea
Processor;
Manmade
Global Weather; Nama For Humanoid;
![]() OS by numbers of versions,
and, in addition to keywords
(e.g. (BE, FE), CE, MS,
M Z,
PE, V M, ... ), TXT for 2 steps ((
OS by numbers of versions,
and, in addition to keywords
(e.g. (BE, FE), CE, MS,
M Z,
PE, V M, ... ), TXT for 2 steps ((![]() verify) verification
(Roaming . Identities . Phone Number)),
verify) verification
(Roaming . Identities . Phone Number)),
![]() WHICH (hub,
WHICH (hub,
![]() I o T,
I o T,
![]() OEM,
OEM,
![]() Router, switch),
Router, switch),
![]() WHEN
WHEN
![]() timestamp
timestamp
![]() user
((login, logout), (sign-in, sign-out)) with web authentication (Web
Authentication a.k.a.
Web A u t h n),
user
((login, logout), (sign-in, sign-out)) with web authentication (Web
Authentication a.k.a.
Web A u t h n),
![]() WHERE location awareness of the phone number,
WHERE location awareness of the phone number,
![]() mochiron of course! 2
(1 mm ones) gravity spots in
mochiron of course! 2
(1 mm ones) gravity spots in
![]() GPS as
embedded
GPS as
embedded
![]() device;
National Security,
Regional Security;
device;
National Security,
Regional Security;
Calendar . Earth . Space . War . HTML;
Automotive Security (e.g. bus'
security, car's security, containership's security, flight security (cargo
plane's security, ("flying car") 's security, passenger plane's security),
ship's security, train's security, truck's security, vehicle's security)
... , using
![]() Artificial Intelligence (IoT,
Location Awareness Response)
... ;
Remark: Security . (360 degree (above
sea level, underwater), radar, sonar) with drones and
Satellite telecommunication, 24/7 (24
hours by 7 days a week) monitoring, ... ;
make no mistake, because 1 accident can cause several millions dollar
liability;
Artificial Intelligence (IoT,
Location Awareness Response)
... ;
Remark: Security . (360 degree (above
sea level, underwater), radar, sonar) with drones and
Satellite telecommunication, 24/7 (24
hours by 7 days a week) monitoring, ... ;
make no mistake, because 1 accident can cause several millions dollar
liability;
embedded;
![]() Radical693;
Radical693;
2565; 2021; this DOMAIN 's Certificate (s) regarding IT (Information Technology) are : (Type . Base-64 encoded X.509, e.g. this DOMAIN .c e r, Option . Current User ), (Type . P K C S #7 Certificates, e.g. this DOMAIN.p7b, Option . Current Machine ) ; Also see: info;
key;
![]() Radical374;
Radical374;
power of the Internet must be peaceful & tranquil;
| 2021 | / | 2565 | ; | security | of | key | : | ||
| 's | web | site | security | , | I F F | certificate | ; | ||
| enhance | d | key | usage | ( | e.g. | ♯.♯.♯.♯.♯.♯.♯.♯ | ) | ; | |
| issue | d | by | ( | e.g. | Secure Hash Algorithm | ( | SHA | ) | ) |
| key | usage | ( | e.g. | digital signature | , | key | code | ) | ; |
| serial | number | ( | e.g. | ♯♯:♯♯ | : | ... | ) | ; | |
| SHA | - | 256 | fingerprint | ( | e.g. | ♯♯:♯♯ | : | ... | ) |
| SHA | 1 | fingerprint | ( | e.g. | ♯♯:♯♯ | : | ... | ) | ; |
| signature | algorithm | ( | e.g. | sha256 | this | DOMAIN | ) | ; | |
| signature | hash | algorithm | ( | e.g. | SHA256 | ) | ; | | | |
| subject | alternative | name | ( | e.g. | DNS | name | , | not critical | ) |
| subject | country | ( | e.g. | country name | , | geographical domain name | ) | ; | |
| subject | locality | ( | e.g. | city name | , | region name | ) | ; | |
| subject | organization | ( | e.g. | company name | ) | ; | | | ||
| subject | public key | ( | e.g. | ♯♯:♯♯: | ... | , | this | DOMAIN | ) |
| subject | public key | parameter | s | ( | e.g. | #### | ) | ; | |
| validation | ( | e.g. | valid from | ( | timestamp | ) | , | | | |
| | | valid to | ( | timestamp | ) | ) | ; | |||
| version | ( | e.g. | whole | number | ); | computer | 's | website | : |
power of the Internet must be peaceful & tranquil;
2891 464195 . 2991573312965
. 171254
:
4 .
8 .
2
:
this DOMAIN .
triangulation .
system ;
![]() OEM Drive (protection on), also see:
Directories;
Files;
OEM Drive (protection on), also see:
Directories;
Files;
one thousand six hundred; e.g.
(![]() 1600,
1600,
![]() 1600,
1600,
![]() 1600,
1600,
![]() 1600)
i.e. Number
1600)
i.e. Number
![]() , (Internal
State Size (bits)) ... , also see:
Action;
NFC IoT;
Number;
Parameter;
Security (computer security, national security,
regional security, satellite security) of this DOMAIN, to be healthy
... ; (
, (Internal
State Size (bits)) ... , also see:
Action;
NFC IoT;
Number;
Parameter;
Security (computer security, national security,
regional security, satellite security) of this DOMAIN, to be healthy
... ; (![]() I/O, a.k.a. (Input, Output), also see:
8iComputer,
5oComputer)
... ;
I/O, a.k.a. (Input, Output), also see:
8iComputer,
5oComputer)
... ;
2565;
2021; Number
![]() ; SHA-3
. Security (
; SHA-3
. Security (![]() Hash) Algorithm ... ;
Hash) Algorithm ... ;
|
|
Internal | State | Size |
|
||||||||
| Output | Size | Input | Size | |||||||||
| Variant | (bits) | (bits) | (bits) | |||||||||
| SHA-3- |
512 |
|
1600 | 512 | 576 | |||||||
| SHA-3- | 384 |
|
1600 | 384 | 832 | |||||||
| SHA-3- | 256 |
|
1600 | 256 | 1088 | |||||||
| SHAKE | 256 | (d) |
|
1600 | d | 1088 | ||||||
| SHA-3- | 224 |
|
1600 | 224 | 1152 | |||||||
| SHAKE | 128 | (d) |
|
1600 | d | 1344 | ||||||
Remark:
Specific Width 480px (because (CRT Screen, VGA Screen) 's Default has been
640x480) since 1990s; Using >
![]() 5 Color,
e.g. ({11,11,11}), ({51,51,51}), ({E3,12,21}), ({E3,E3,E3}), ({FF,CC,99}), Aqua
Color, Navy Color, ... ;
this DOMAIN is beyond "Blue LED"
... , regarding Security; before installing this DOMAIN 's
contents, measure your device's weight (s)
... , because Gravity Dimension Computer is ... ; weight (s) of
(BE vs. FE) may vary, depending upon directional of gravity spots,
number of gravity spots, sizes of gravity spots, ... ;
National Security;
Regional Security;
5 Color,
e.g. ({11,11,11}), ({51,51,51}), ({E3,12,21}), ({E3,E3,E3}), ({FF,CC,99}), Aqua
Color, Navy Color, ... ;
this DOMAIN is beyond "Blue LED"
... , regarding Security; before installing this DOMAIN 's
contents, measure your device's weight (s)
... , because Gravity Dimension Computer is ... ; weight (s) of
(BE vs. FE) may vary, depending upon directional of gravity spots,
number of gravity spots, sizes of gravity spots, ... ;
National Security;
Regional Security;
five hundred and twelve (![]() 512) e.g. in square design model, WHEN 3/4 is on, 1/4 should be off, so, 512/4
means 4 quantity of 128; Also see:
6fComputer;
Number;
Security;
512) e.g. in square design model, WHEN 3/4 is on, 1/4 should be off, so, 512/4
means 4 quantity of 128; Also see:
6fComputer;
Number;
Security;
2565;
2021; Number
![]() ; SHA-2
. Security (
; SHA-2
. Security (![]() Hash) Algorithm ... ;
Hash) Algorithm ... ;
|
|
Internal | State | Size |
|
||||||||
| Output | Size | Input | Size | |||||||||
| Variant | (bits) | (bits) | (bits) | |||||||||
| S H A- |
512 |
/256 | 512 | 256 | 1024 | |||||||
| S H A- | 512 | /224 | 512 | 224 | 1024 | |||||||
| S H A- | 512 |
|
512 | 512 | 1024 | |||||||
| S H A- | 384 |
|
512 | 384 | 1024 | |||||||
| S H A- | 256 | 256 | 256 | 512 | ||||||||
| S H A- | 224 | 256 | 224 | 512 | ||||||||
Remark:
Specific Width 480px (because (CRT Screen, VGA Screen) 's Default has been
640x480) since 1990s; Using >
![]() 5 Color,
e.g. ({11,11,11}), ({51,51,51}), ({E3,12,21}), ({E3,E3,E3}), ({FF,CC,99}), Blue
Color, Green Color, Yellow Color, ... ;
this DOMAIN is beyond "Blue LED"
... , regarding Security; before installing this DOMAIN 's
contents, measure your device's weight (s)
... , because Gravity Dimension Computer is ... ; weight (s) of
(BE vs. FE) may vary, depending upon directional of gravity spots,
number of gravity spots, sizes of gravity spots, ... ;
National Security;
Regional Security;
5 Color,
e.g. ({11,11,11}), ({51,51,51}), ({E3,12,21}), ({E3,E3,E3}), ({FF,CC,99}), Blue
Color, Green Color, Yellow Color, ... ;
this DOMAIN is beyond "Blue LED"
... , regarding Security; before installing this DOMAIN 's
contents, measure your device's weight (s)
... , because Gravity Dimension Computer is ... ; weight (s) of
(BE vs. FE) may vary, depending upon directional of gravity spots,
number of gravity spots, sizes of gravity spots, ... ;
National Security;
Regional Security;
2018/2561;
(for each Time Zone, for each local system) using
Artificial Intelligence (to do good, to be better secure environmental) i.e.
security ... ; SQRT2 design model:
![]() okonau Do beyond (font, layer, SPL) system security (16 bit, 32 bit, 64
bit, 128 bit, 256 bit, 1K bit, 4K bit, 8K bit, ... ) Q&A, ... ;
okonau Do beyond (font, layer, SPL) system security (16 bit, 32 bit, 64
bit, 128 bit, 256 bit, 1K bit, 4K bit, 8K bit, ... ) Q&A, ... ;
03/01/2018 /2561; this DOMAIN 's compilation number: version C118; Global Sign certificate (e.g. this DOMAIN . p7b FILE i.e. (..\..\IT\25620\Certificate\this DOMAIN.p7b)) WHICH has been created and installed for its System Security, using SONY 4K TV with HDMI connection, and NFC with SONY X Z smart phone; with Mini Dictionary (i.e. \\ Mini Dictionary \ *.* /s) contains approx. 6714 Files, 171 Folders, 58.1 MB (60,948,727 bytes) Size, and 3400+characters available to learn and understand;
partition; wall;
![]() Radical381;
Radical381;
Since
2017/2561, using
 Walls, for better
system security ... ;
Walls, for better
system security ... ;
- guard and secure system number of smart sensing and IoT operation ... ;
- protect real time system of airline flights, by using iroColourWaveForm ... ;
- verify iroColourWaveForm color codes, And Then, guard and secure system number ... ;
Since
2017/2561, for each
![]() Time Zone, this
DOMAIN, using AI, in the Internet (High-bandwidth Digital Content
Protection,
Time Zone, this
DOMAIN, using AI, in the Internet (High-bandwidth Digital Content
Protection,
![]() H D C P)
... ;
H D C P)
... ;
Since
2013/2557, this DOMAIN
has
designed
& developed
its system security to
Sound
![]() Pressure
Pressure
![]() Level
Level
![]() Security (
Security (![]()
![]() ID)
... ;
ID)
... ;
Time must be
understood 1st,
![]() and then
and then
do computer systems security ... ;
![]() 3 common
3 common
![]() methods
exist:
methods
exist:
1,
establishing sub-tree;
2,
![]() modeling individual entry,
e.g. in 2006, for each 480 Mbps pipe till 30 pipes @ 30 M
c/s (Hz) USB D W A ...
;
modeling individual entry,
e.g. in 2006, for each 480 Mbps pipe till 30 pipes @ 30 M
c/s (Hz) USB D W A ...
;
3,
modeling attributes of
each entry;
802.* specific; 802.* specific: in 2006, 802.1x product specific are E A P-FAST, E A P-TLS, E A P-TTLS, LEAP, P E A P, and etc.
A CAP;
ACE;
AC K; (ACL
One of the
Control Lists (Wire speed) (...)); A E C 128
C CM
encryption, LSI
D W A USB wire AND
wireless, 32 pipes support at 30 MHz;
A E S;
AES 256-bit encryption, also see:
CBC mode;
AH
AH OR ESP;
using artificial intelligence 26 secure Ajax proxy (XML Http Request) ... ;
ANS1 USA; ARP; ATP; (Authentication (User account (*FS mount access)) (Password (Good password) (Shadow password)) (Permission (Directory) (File) i.e. s u id, s g id in Linux) (...)); AV X, 256-bit, Win7 SP1;
b00tp, B00t Pr0t0c0l;
BSD Meta system Integration specification AND
U-Prove Cryptography specification;
Basic understanding of
![]() HOW security
works is: 1st, copy a noCOOKIE browser file i.e.
no
COOKIE
.exe into a USB Drive; 2nd, open the
USB Drive among computers ... ; 3rd, to do
right click
HOW security
works is: 1st, copy a noCOOKIE browser file i.e.
no
COOKIE
.exe into a USB Drive; 2nd, open the
USB Drive among computers ... ; 3rd, to do
right click
![]() on
the noCOOKIE ... ; Notice THAT there is no
Security Tab prompts, because not yet to be defined
e.g. object,
on
the noCOOKIE ... ; Notice THAT there is no
Security Tab prompts, because not yet to be defined
e.g. object,
name,
... , at THIS time; Now is the time to basic understand
![]() WHAT is security, to do so, copy
noCOOKIE into a system drive's directory, right click on i.e. C:\
IT
\
Executable
Application
\
no
COOKIE
.exe ; if Compatibility
prompts, choose local system's version e.g. 95, 98, NT, XP, Win7, ...
>> Properties >> Security >> ... names >>
Advanced >> Advanced Security
Settings for noCOOKIE >> Edit... >> Add... >>
WHAT is security, to do so, copy
noCOOKIE into a system drive's directory, right click on i.e. C:\
IT
\
Executable
Application
\
no
COOKIE
.exe ; if Compatibility
prompts, choose local system's version e.g. 95, 98, NT, XP, Win7, ...
>> Properties >> Security >> ... names >>
Advanced >> Advanced Security
Settings for noCOOKIE >> Edit... >> Add... >>
![]() object
>> Check names >> OK; You have just managed group
object
>> Check names >> OK; You have just managed group
or user,
by using "name" parameter configuration within your domain system ... ;
![]() BIOS;
BIOS;
Building Security
In Maturity Model (
![]()
![]()
![]() B S I M M), also see: http://b s i m m .com;
BSIMM6;
B S I M M), also see: http://b s i m m .com;
BSIMM6;
cable lock slot; CA; CAP T C H A, Completely Automated Public Turing test to tell Computers and Humans Apart;
using artificial intelligence 26 secure cap t c h a s ... , for GET/POST requests ... ;
CD;
CERT
USA;
Certificates, also
see: this DOMAIN 's
certificate;
![]() cipher
(PIN,
Personal Identification Number); CIPHER UNICORN-A, NEC's
A E S D E S, interface;
Cisco specific; C o m p u trace, theft
protection agent in BIOS, by Panasonic Tough Book; C0PPA, Ch1ldren 0nl1ne Pr1vacy
and Pr0tect10n Act
USA;
C F S
It supports local and remote;
Core Dump Size limitation;
cipher
(PIN,
Personal Identification Number); CIPHER UNICORN-A, NEC's
A E S D E S, interface;
Cisco specific; C o m p u trace, theft
protection agent in BIOS, by Panasonic Tough Book; C0PPA, Ch1ldren 0nl1ne Pr1vacy
and Pr0tect10n Act
USA;
C F S
It supports local and remote;
Core Dump Size limitation;
Cisco specific: 2006 line security ohm · meter products are Clean Access, A C S, A S A, CSA, IPS, Pix, and etc.; 2006 wireless security dB · meter products are Controller specific, I OS AP, Light Weight AP, U CS, and etc.
using artificial intelligence 26 secure Confine un trusted content i.e. <i frame> ... ;
using artificial intelligence 26 secure Cross-site request forgery (i.e. CS R F) ... ;
using artificial intelligence 26 secure Cross-site scripting (i.e. X S S) ... ;
using artificial intelligence 26 secure Cryptographic server identity (i.e. locked SOP) ... ;
using artificial intelligence 26 secure cryptographic tokens ... , for GET/POST requests ... ;
AI
![]() verify
verify
![]() computers
e.g.
computers
e.g.
![]() info
info
![]() code (63626066673658558569584)
i.e.
code (63626066673658558569584)
i.e.
![]() ASEAN
ASEAN
![]() cyber
security; Also see:
Satellite DNS System;
cyber
security; Also see:
Satellite DNS System;
By
![]() WORMHOLE
WORMHOLE
(
for
![]() each
each
![]() surface
95
285
surface
95
285
![]() Internet)
... ;
Internet)
... ;
AI
![]() verify
verify
![]() computers
... ;
computers
... ;
D AC L One of the Control Lists; D D P; DES; D H C P; Difficulty levels: The most difficult system security level is Pin level security > System Menu level security is less difficult than Pin level security > System DB Key level security is less difficult than System Menu level security > Script level security is easiest and commonly available; DNS H0st names ≠ 1P addresses; (DNS server query limitation (Controlling recursive query) ); (DNS SEC (KEY record (A/C) (N AM T Y P) (SIG) (XT)) (...) ); D0S, Den1al-0f-Serv1ce, Unit = S Y N /s; D S A;
using artificial intelligence 26 secure Dynamic (DNS) ... ; Dynamic Frequency Selection;
E F S; (Encrypt10n (Bl0ck C1pher 1.e. D E S 's 64b1t bl0ck w1th 56b1t key;) (Stream C1pher) (...)); E I G R P; E K U and E K U O ID; Environmental variables Also see: share characters;
using artificial intelligence 26 secure Escudo Web protection (e.g. ACL s, CS R F, X S S) ... ;
using artificial intelligence 26 secure 285 e v a l() function (i.e. J SON) ... ; Avoid;
FCC; F CS Ethernet; Filtering port number; Firewall/VP N [Develop the unit's characteristics], Firewall coexistence DNS server; FTP;
Firewall specific services oriented security rules:
[Remark: 1st to understand Internet vs. Proxy Server Settings, otherwise following contents may not be understandable; For Internet/Intranet security, also see: IANA 2007 standard Keyword to Port Number]
If IC MP type =
source
quench, and then
;
If IC MP type = echo request
interface
= Ext, and then
;
If IC MP type = echo reply
interface
= Ext, and then
;
If IC MP type = destination
unreachable
interface
= Ext, and then
;
If IC MP type = service
unavailable
interface
= Ext, and then
;
If IC MP type = TTL exceeded
interface
= Ext, and then
;
If IC MP type = parameter
problem
interface
= Ext, and then
;
If IC MP type = echo request
interface
= I n t, and then
;
If IC MP type = redirect
interface
= Ext, and then
;
If IC MP type = echo reply
interface
= I n t, and then
;
If IC MP type = destination
unreachable
interface
= Ext, and then
;
If IC MP type = service
unavailable
interface
= Ext, and then
;
If IC MP type = TTL exceeded
interface
= Ext, and then
;
If IC MP type = *
interface
= *
interface
= *, and then
;
If IC MP type = *
OP =
source route, and then
;
If IC MP type = *
interface
= Ext
source IP = internal, and then
;
If IC MP type = *
interface
= I n t
destination IP = internal, and then
;
If IC MP type = *
interface
= Ext
destination IP = protected servers, and then
;
If IC MP type = *
interface
= Ext
destination port = RIP, and then
;
If IC MP type = *
interface
= Ext
destination port = OS PF, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 0 ~ 20
Type =
U D P, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 6000
Type =
U D P, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 6001
Type =
U D P, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 6002
Type =
U D P, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 6003
Type =
U D P, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 161
Type =
U D P, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 162
Type =
U D P, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 0 ~ 20
Type =
TCP, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 6000
Type =
TCP, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 6001
Type =
TCP, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 6002
Type =
TCP, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 6003
Type =
TCP, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 161
Type =
TCP, and then
;
If IC MP type = *
interface
= *
interface
= *
destination port = 162
Type =
TCP, and then
;
If IC MP type = *
interface
= Ext
interface
= *
destination port = 23
Type =
TCP, and then
;
If IC MP type = *
interface
= Ext
interface
= *
destination port = 8080
Type =
TCP, and then
;
If IC MP type = *
interface
= Ext
interface
= *
destination port > 1023
AC K = C
Type =
TCP, and then
;
If IC MP type = *
interface
= Ext
interface
= *
destination port = 20
AC K = C
Type =
TCP, and then
;
If IC MP type = *
interface
= Ext
interface
= *
destination port = 21
AC K = C
Type =
TCP, and then
;
If IC MP type = *
interface
= Ext
interface
= *
destination port = 25
(destination IP ≠ SMTP server)
Type =
TCP, and then
;
If IC MP type = *
interface
= Ext
interface
= *
destination port = 80
(destination IP ≠ Web server)
Type =
TCP, and then
;
If IC MP type = *
interface
= Ext
interface
= *
source port = 80
destination port > 1023
AC K = S
Type =
TCP, and then
;
If IC MP type = *
interface
= I n t
interface
= *
source port > 1023
destination port = 80
Type =
TCP, and then
;
If IC MP type = *
interface
= *
interface
= *
source IP = NNTP server
destination IP NNTP server
Type =
TCP, and then
;
If IC MP type = *
interface
= *
interface
= *
source IP = NNTP server
destination port = 119
Type =
TCP, and then
;
If IC MP type = *
interface
= *
interface
= *
source IP SMTP server
destination port = 25
Type =
TCP, and then
;
for
each
![]() time
zone,
time
zone,
for
![]() each
each
location,
home
![]() security by
security by
humanoids,
also see: Nama
For Humanoid,
![]() HOW to punish
(e.g.
HOW to punish
(e.g.
![]()
![]() )
unauthorized
)
unauthorized
![]() trespass
trespass
person;
using artificial intelligence 26 secure HTML validation ... ;
using artificial intelligence 26 secure 285 Http Only cookie attribute (i.e. grant access 26 cookies from 15 HTTP request) ... ;
![]() HOW to
determine (foe
or not), also see: enemy; foe; opponent;
HOW to
determine (foe
or not), also see: enemy; foe; opponent;
![]() Radical745;
Radical745;
_ IFF
virus, EXE
Anti Virus;
system
(![]() )
security
system ... ;
)
security
system ... ;
![]()
![]() 1??1G, also see:
Bus Connector and Port; Schematic Symbols;
1??1G, also see:
Bus Connector and Port; Schematic Symbols;
IKE; 1MAP; 1SP; 1P; (1P Address Ass1gnment (Manual) (Aut0 b00tp) (Dynam1c b00tp D H C P)); i p chains Controlling access; 1PC1S; 1PSec; 1RC; I R F; I R M; is 1 new cloud - based security control layer 669 browsers; ISMS, INFORMATION SECURITY MANAGEMENT SYSTEM, 1S0; 1V;
using artificial intelligence 26 secure J SON P script tag injection ... ;
(K DC (T G T)) MIT's Kerberos authentication; Kernel configuration; Keyword to Port Number;
L2TP;
lm hosts security initialization;
![]() local;
L S A;
L S P;
LU1D;
local;
L S A;
L S P;
LU1D;
MAC; mask; M1B; M1ME; (M0dulat10n (AM) (FM) (PC M) (...) Als0 see: S/N 1n UN1T);
using artificial intelligence 26 secure M o z i l l a Content Security Policy (i.e. CS P) ... ;
(named running (CH ROOT jail) (without ROOT privilege))
DNS server;
NAT;
N B P;
N C P;
NetB10S; NetWare
system usages;
N F S; (N1ST
(S H A N0t
ava1lable 1n publ1c) (SHA-1)
(S H A-*) (...) );
NNTP;
N OS;
N S A;
numerological dimension a.k.a.
a k a .INF;
Note for security novice: Automata theory is
recommended to read because relation between handshakes and
communication between computer machines
sometimes are abstract to common people; Once abstract
can be overviewed, twist-and-turn in cryptanalysis and cryptography becomes a
little easier ... ;
optional finger printer reader; 0SPF; O U;
password security; Peculiar mind reminder: O01I, IOl0
i o L zero, *$,
" '', ... ;
P2P;
P0P;
P P D D; (P P T P
(PPP) (...) );
Public Key Token,
matrix of base16 hexadecimal and 16 characters where: If Time AND Possible value
matches And Then Assembly Cache = TRUE;
|
|
|||||||||
|
|
|
|
|
|
|||||
|
|
|
|
|
|
|||||
|
|
|
|
|
|
|
||||
|
Also see: Action; Protocol and Port; Security; |
|||||||||
( Half
Duplex Memory Architecture,
one direction only) . POP is very useful to pop messages (MSG) from Server
to its User, and POP can be very useful
to do (e.g.
DIAL CALL,
Emergency Alert,
New Notification,
NFC IoT ID,
NFC RFID,
Weather Alert,
System MSG,
... ) ... ;
Remark: Global (1000) limits Remote (100) limits (Local (10) Dial Call Number)
to do pop messages (MSG); other wording would be: SQRT2 (±98)
floating points' Latch 3 limits Latch 2 limits Latch 1;
Quantum cryptography (Stable key generation (Q B E R)); (Q o S (Application Q o S OS I application level priority) (Port Q o S Specific port enable OR disable; ingress OR egress) (Voice Q o S) (...));
RAD1US; Recommended website: www .c cc .go .jp;
*$ is wildcard * AND share character $ i.e. $HOME, $PATH, ADMIN$, C$, D$, F$, S$, I PC $, PRINT$, SYS V O L $, ... , also see: variable; [SEC];
S A C L One of the Control Lists; SAM; Samba Server;
using artificial intelligence 26 secure Scanning tools and services (e.g. SQL or DO M X SS) ... ;
S CC M L; s Flow traffic
Monitor by Foundry Network;
S1D;
SK1P;
S LIMIT-C
wireless e-mail filter;
SMB
C2MYAZZ, LAN MAN authent1cat10n;
SMTP
ASC11 text 0nly;
SNMP
SNMP agent and
1ts management: Als0 see:
M1B; Split
namespace Public
OR private;
Spread spectrum;
SPX;
S S H;
![]() SSL
SSL
![]() SSL3 1s TLS pr0t0c0l;
SSL3 1s TLS pr0t0c0l;
![]() s s l ciphers
s s l ciphers;
S Y N; sys log utility
sys log .conf
file in
Linux; Systems security links: Also see:
File Systems;
System time stamp;
swatch
Perl
script;
![]() verify connection's integrity:
verify connection's integrity:
- security certificate, using a strong signature;
- security certificate (name of the page you are trying to view);
- security certificate is from a trusted certifying authority;
- security certificate has a valid name matching;
- security certificate has expired;
- security certificate is not yet valid;
Security of Stock; e.g.
![]() anzensei
Security (in trading
Stock (s)) secure listed
companies' symbols, doko
anzensei
Security (in trading
Stock (s)) secure listed
companies' symbols, doko
![]() WHERE
banks are making money by (buying,
selling)
of stocks ... ;
WHERE
banks are making money by (buying,
selling)
of stocks ... ;
TCP;
TCP Wrapper Samba
Linux; in et d; x in et d; TCP/IP; TCP/IP
protocol stack embedded IC chips; T D S,
encryption
System certificates;
TLS;
TPM security ship v♯
; TTL;
this DOMAIN 's Security (Global Security, Regional Security, National Security), also see: Inductance;
U D P; u mask configuration; updates is Edit | Preferences... | Startup. 333+ of Preferences... exist, i.e. temp is one of the Preferences...'s options; UPS; URL;
using artificial intelligence 26 secure un-trusted data (e.g. post input, query strings, URLs) ... ;
USA (United States of America) National
Security (e.g. NOT
to happen 2+ hours of overwriting & resetting GPS of automotives)
... ;
USA's National
Security,
protected by
![]() Rakhine American
Ace Jaw,
e.g.
Rakhine American
Ace Jaw,
e.g.
![]() IFF (hack,
hacked,
hacker,
hacking)
is defined
by
IFF (hack,
hacked,
hacker,
hacking)
is defined
by
![]() cyber , remotely burning
the defined
(hack,
hacked,
hacker,
hacking)
computer's
motherboard physically (using
military grade multi long length
WORMHOLE way laser)
... ; power of the Internet must be peaceful & tranquil;
using insectoid reports to animaloid reports to humanoids to mark ... ;
USA (United States of America) National
Security (e.g. NOT
to happen
cyber , remotely burning
the defined
(hack,
hacked,
hacker,
hacking)
computer's
motherboard physically (using
military grade multi long length
WORMHOLE way laser)
... ; power of the Internet must be peaceful & tranquil;
using insectoid reports to animaloid reports to humanoids to mark ... ;
USA (United States of America) National
Security (e.g. NOT
to happen 2+ hours of overwriting & resetting GPS of automotives)
... ;
W E P (64 bit) (128 bit); wh01s rs.1ntern1c.net; W1reless T0p0l0gy; W MP Info .xml;
''Y0u kn0w" ''when" ''y0u kn0w what y0u d0 n0t kn0w ... ; A1s0 see: Instruction Segment; Netw0rk Des1gn Pr1nc1ples; Pr0t0c0l and P0rt; Scripts;
Zone transfer restriction DNS server;
...
舰㠂आ蘪虈܁ꀂʂ〩ʂȥā1ରआ蘪虈܁ꀁʂ」 ʂ〉 Ƃꁶȃ ȁဂꛑё栻꼍Ꝍ軐퓱ꅹरԆหȃԝㄘ〖ؔ唃ഓ摁業楮瑳慲潴ひᜠ」〹ㄲ㐷〱娲༘ㄲ㤰㜱㜱ㄴ㈰ずㄘ〖ؔ唃̄ഓ摁業楮瑳慲潴ひ龁ര आ蘪虈āԁ̀趁要脂沥ꀟ☟贊囇囬乿넵髇쯶㨃麙蛸蔜솙踠㰳㾡⊦潎쯮O밍ギ怆啸푍黟䔂揀䋉織녙ꦂ䨘氶��띍謄ᅍ埭ꅭ擺혛��臨缸᠏��偏熂ഥ䂮♯紏ࡷ袝ᔢⓄ姠攜֣̂ꌁずじؕ唃┝คర ਆ ث Ё舁Ѓ㐰ᵕБꀫة⬊Ć Ą㞂Ȕꀃఛ䄙浤湩獩牴瑡牯啀䅓奍乁䅍R र̆ᵕ Г。 ̎ᴂ 脃ꊉ煌듼ﺎ⟲捦胎ᶧ쀘䵯䪠ꮱ㵸㑠钨㖃須춹ꄆꥉ諓㽑䀰˅ꜭ貕賄㔲㿄旐츧䠔ɟ큻์癸뽣娜릫惧뼤宬桦㷒ʐ㮉섮祑ȝ㬢椖娘ᖅϩ왱㉷Ȣ1
|
|
|